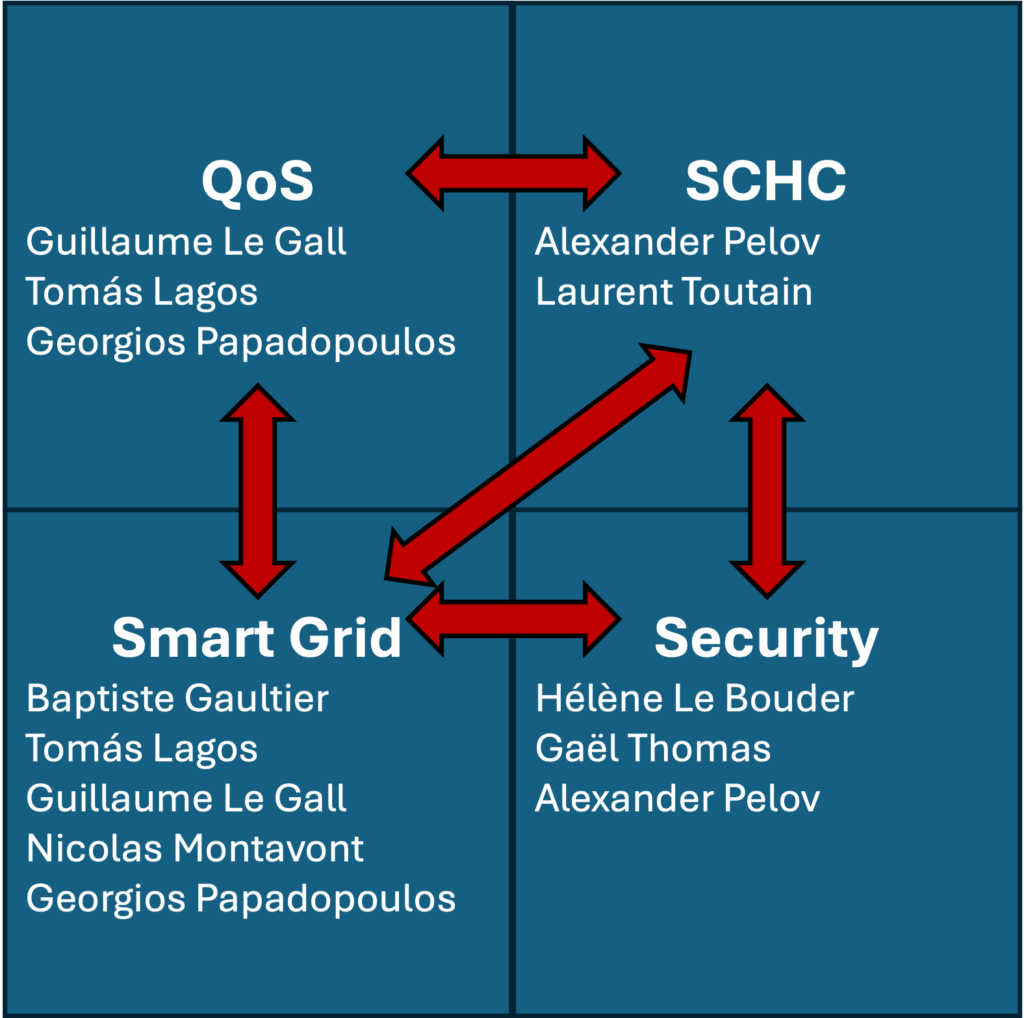
The OCIF (Objets Communicants pour l’Internet du Futur) research team at the IRISA Laboratory focuses on protocol architectures for the Internet of Things (IoT). Part of IRISA’s Department D2 (Networks, Telecommunications & Services), OCIF develops solutions bridging current Internet technologies with emerging needs in IoT. Their research spans internet architecture, auto-configuration in dynamic low-power and lossy networks, energy management, and security strategies.
Applications include smart grid, Industry 4.0, and smart city infrastructures. The team investigates solutions to adapt the OSI and TCP/IP protocol stacks to the specific constraints of IoT devices by contributing with lightweight protocols (e.g., SCHC), and contributes on routing algorithms and medium access methods for low-power wireless mesh networks.
Founded in December 2024, co-located at IMT Atlantique (campus of Rennes) and University of Rennes, OCIF actively continues to shape robust, scalable, and secure IoT architectures compatible with existing Internet frameworks.
The key areas of research for OCIF include: